By: Michael-Roger Wright
Revisiting the past
Communications Security
Extending brand reach with the Xerial platform
Secure managed data solutions
Managed reporting features
AP Load Balancing and resource allocation
Data-Sharding and other data management techniques
Built-in Counterfeit Protection
Hyperledger Fabric and Blockchain Integration
PISC – Product Identifying Serial Codes
Converting PISCs into 1d or 2d barcodes
XerialOS Framework and API
Modules and Templates
Reassessing History:
Over the past three decades, we have witnessed unparalleled advancements intertwined with regrettable regressions concerning the prospect of a decentralised Internet. For many, our Internet experience is primarily orchestrated through intermediated services and utilities. These are fashioned to administer our individual user IDs, account names, images, rich media posts, and other data, subsequently merging them into branded services colloquially referred to as social media.
The Internet, rooted in its ARPANET origins in military and regional academic institutes, was designed as the ultimate communication distribution network and subsequently made available for public usage. In the early 1990s, firms such as AOL, Compuserve, and Netscape unveiled competing internet browsers, ostensibly promoting the free exchange of thought and ideas.
These applications aimed to construct a safeguard against any single company or entity imposing excessive, restrictive controls upon its users. This safeguard was intended to shield individuals from political or nationalistic/fascist perspectives by fostering a socially monitored network for the unrestricted dissemination of ideas and information within a public forum.
These foundational principles, instrumental in shaping Internet policy, are increasingly vital in the present day. They must resist the coercion imposed by certain authoritarian business models or political views, which once more threaten to suppress freedom of thought, open dialogue, or political discourse. It is critical to recall that the founders envisaged entitlements to facilitate the free exchange of ideas and information as a countermeasure against those who would obstruct legally protected content on their public platforms. While we may not concur with or appreciate what we observe or hear, if it doesn’t contravene the law, it should be upheld as free speech.”
How did we arrive at this juncture?
The inventions that gave birth to the Internet are a melange of intricate systems demanding years of skill acquisition to master. The meteoric rise of social media platforms is largely due to their designed simplicity, which enables users to express their views while providing the network and content management layers for uploading, sharing, and viewing rich media assets. These assets encompass databases of graphics, videos, texts, code and data, as well as manage the interaction between parties.
Just as not everyone possesses the expertise required to inaugurate and operate successful IP-based Internet services, there remains a potent desire to engage with the social pool that often provides the support and nurturing that is lacking in physical reality. Each of us harbours the wish to share our insights and daily experiences with others who might have similar interests in the human condition. At times, this necessitates responsible individuals pushing the envelope of social acceptability, thus paving the way for future norms.
As emotional beings, we are proficient at finding acceptance amongst our peers when the restrictions of a technical learning curve are supplanted by personally enriching experiences. The complexity of delivering a competitive experience is a daunting task that deters most individuals. It is usually the early market leaders who set the rules, with technological innovation propelling adoption. However, this should not prevent us from upholding and reaffirming our inherent rights to free speech and expression, regardless of our position on the political spectrum.”
“Xerial Extensions: Solutions for Decentralizing Brand Reach
Xerial extensions provide solutions for brand holders who wish to directly extend their brand reach to customers. The platform is constructed atop server-side applications, connected to the mobile UI via a series of custom APIs. These APIs are designed to simplify the management and dissemination of marketing assets, and to enhance security and prevent counterfeiting of a manufacturer’s brand assets.
Xerial modules are constructed using an extensible framework. This design is intended to future-proof the delivery of marketing assets against future iterations of enhanced services and features. Product data is collected from easy-to-use, form-based inputs that link directly to the data store through identifiers termed ‘Product Identifying Xerial Codes.’ These codes, printed directly on product packaging, provide unique identifiers for products at the individual or SKU level.
Furthermore, Xerial integrates the use of Machine Learning and AI-enhanced tags built around shelf-edge technologies associated with the product within the retail environment. Xerial automates the assembly of managed and trackable data stores of information right at the client’s mobile smart device. The Xerial platform oversees all aspects of network performance, content streaming, data handlers, and data management to offer your end-user a world-class service experience through a high-quality UI or mobile app interface, tailored specifically to the brand holder or client.
Xerial revolutionizes the flow of information by developing smart applications that detect the server resources being utilized, thereby ensuring a minimum quality of service. This managed layer reduces overall resource loads by allowing them to run from their own protected memory space. By keeping services separated, the platform helps prioritize resource-intensive, on-demand services, such as streaming video, while allowing smaller loads, such as text or data-related services, to remain unaffected.
Learn more about these platform extensions below.”
The Xerial Product Management Layer:
Tailoring Information Flow to Enhance User Experience.
The primary task of the Xerial product management layer involves the creation, management, and routing of product information and rich media content for each product. Each unique product ID is recorded in a master data record, identified by linking the product ID back to the data-store containing information specific to that product. When a mobile user scans the product identifier, the Xerial App can locate the data-store and begin delivering the data instantly to the requesting device.
Additional content layers can be simultaneously streamed to the requestor using algorithms designed to measure specific server loads. Upon reaching a predefined load threshold, such as a spike in user demand for a video stream, the server instantaneously replicates and disseminates the profile and content to servers located in higher-demand regions, thereby establishing a Quality of Service (QoS) that rivals major on-demand video services.
Consider this example: data streams using H.264 compressed 4K videos, streaming to four million users at varying start and stop times, necessitate significant server resources. The program’s algorithms will replicate the video stream for each client starting at different times. To create a visual: it’s the difference between a cable channel always starting a video broadcast at one fixed time and an on-demand service where you choose when to start the video.
Xerial operates as an ‘Enterprise Resource Platform Extender’, linking cloud-based information services to the existing POS system. It combines SKUs and inventory with a B-Channel of information solutions. In essence, the platform creates an organic link between the product and client-managed information stores for data delivery. This content can be easily delivered to mobile, stationary, and desktop devices, including consumer television and direct-to-vehicle in-motion systems. New delivery options are virtually unlimited.
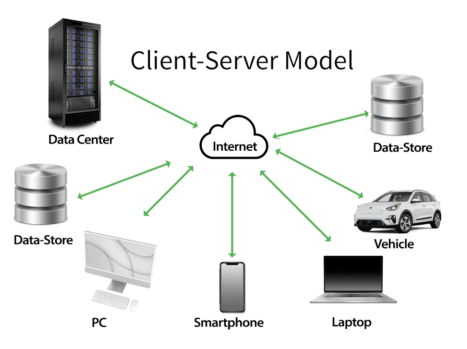
Companies such as IBM first popularized the client-server model, using terminals linked back to a central host server, enabling data from the server to run directly on the terminal machine. Xerial extensions operate similarly, where the terminal client is the mobile app, but with the distinction that data is separated into manageable service profiles. The program queries data based on resource usage profiles. It’s a novel approach, but when freed from the limitations of a centralized service platform, you discover capabilities that until now were nearly impossible to achieve outside of platform policies.
Welcome to what’s next.”
Xerial: An Enterprise Resource Platform Extender Facilitating Information Delivery
Xerial is an Enterprise Resource Platform extender that seamlessly links information stored in cloud-based data-stores to application services, designed as an extension to the existing Point of Sale (POS) systems. This platform integrates SKU’s and inventory with product-specific promotions, advertisements, information stores, and a comprehensive knowledge base of information to create a B-Channel for content delivery.
In its most fundamental form, the platform establishes an organic link between products and new information stores, thereby enabling efficient information delivery to clients. This streamlined process not only enhances the user experience but also optimizes the marketing potential of product information, advertising, and promotions.”

User-Centric Action Capturing and Branding Opportunities through Xerial Extensions
User interactions with your content are captured through Customer Relationship Management (CRM) triggers in real-time. The resulting data is stored directly within the product database and can be retrieved through Xerial’s comprehensive reporting features. Data points are isolated and transformed into report elements that are only activated when a user engages with specific aspects of the product presentation. This sophisticated reporting system allows you to discern which videos, graphics, content, coupons, and shares are linked to specific products globally at any given time, inclusive of user location down to the city, country, and time zone level.
The primary goal of this approach is to measure content effectiveness, thereby equipping brand holders with valuable insights into user behavior and consumer psychographics. To maintain user privacy and security, this data is always protected and captured only with prior user authorization.
Xerial’s enterprise extensions empower you to place your brand materials, coupled with the CRM tools, in previously unimagined contexts, courtesy of our Internet of Things (IoT) software extensions. Company founder, Michael Wright, perfected these methods and filed for patent protection in 2014. The technology used in Xerial and Enterprise Resource Planning Extensions (ERPe) was granted a U.S. Patent in 2018. These patented methods are incorporated into the Xerial enterprise server software, desktop, and mobile app, facilitating a novel approach for product identification and simultaneous multi-channel data capture, thereby creating a truly omnichannel experience.
The functionality of this technology and the associated patent mirrors the recognition process of barcodes by a Point of Sale (POS) system. However, instead of merely tracking Stock Keeping Units (SKUs) for inventory purposes, our focus also extends to delivering media and information assets over the internet. We achieve this by using Product Identifying Serial Codes (PISC) as product identifiers, which enable the mobile app to locate the datastore in the cloud. This method offers an organic link back to the product that is almost unparalleled.

Counterfeit protection
Xerial has been engineered with advanced security automation features, whereby its algorithms can determine whether a Product Identifying Xerial Code (PISC) is replicated, counterfeit, expired, or linked to a decommissioned product identifier. When a user scans a product identifier, the associated serial code is transmitted to the Xerial server for validation against its securely stored master record within the product’s database, and this transaction is logged in the system’s file.
If the serial code matches the stored record, the system triggers an automated response to the mobile device, indicating that the item is active, registered in the system, and permits the execution of the next pre-set instructions as part of the security algorithm sequence.
Should the serial code fail to match after several scanning attempts, a predefined response protocol is enacted, blocking and reporting the failed code attempt. This feature enables the system to document and locate the unsuccessful scan for further investigation. For instance, Xerial codes provide connections to User Interface (UI) elements that assure customers of the validity of their purchase. If the code doesn’t correspond to the stored data record, the system activates a rejection notification, which appears in a modal window on the user’s mobile device. It clarifies that the scanned item is not registered with a valid serial code and restricts user interactions to a predetermined set of instructions prior to providing access to the item’s master data store.
With the server-side operation of these algorithms, before establishing a connection to the data store, SQL data injection scripts cannot be processed by the server. This is because these transactions are not housed within the same node. Unless the client can crack a blockchain at each connection between shards within the system, there is a natural immunity against a myriad of potential threats.
Even in the unlikely event of a malicious actor gaining user administrative access to create a data store related to a PISC, there are no assets on the client device capable of running malicious code from a precompiled app. Furthermore, such an action would be confined to only one PISC data store and would not grant access over the core functions of the platform, thereby further constraining any potential malicious content loads.”
“As a product brand’s viewer base expands, the data schema may need to evolve to support users in certain situations. Xerial operates industry-leading data handlers, employing our custom-designed extensions and modules in the background to manage the integration and delivery of content to each client. This liberates our clients’ resources, allowing them to be repurposed towards enhancing the user experience.
For instance, when constructing your service profile, you may initially set it up to store user profiles and emails within the same sector of your database. As your user base proliferates, the need to integrate additional resources like larger storage drives becomes inevitable to sustain this growth, demanding more resources and time for management.
In dealing with aging infrastructure, challenges like these often lead to service downtimes, especially when it’s necessary to remap user modules to the new data store structure to alleviate the demand on limited resources. Xerial is built atop more than 35 fully customizable APIs and hundreds of open-source extensions, each divided into service profiles and operating within protected memory spaces. These APIs dynamically connect the user experience to the core enterprise software during the creation of their mobile or desktop experience.
Each profile amasses resources to efficiently deliver the user experience from the data stores designated by the client. Xerial also integrates hundreds of open-source modules that constitute the Xerial enterprise framework. This framework is structured around an extensible architecture, ensuring the continuous addition of new extensions to future-proof the marketplace’s standards.
Your services shouldn’t suffer, for example, from reduced video streaming performance because they share the same network with a gaming platform catering to a hundred million users and consuming a larger chunk of network resources. Server resources and data are never pooled in commonly-used service profiles that strain server resources while your brand experience bears the brunt. Performance is key to an exceptional user experience, and this is where the Xerial Platform excels.” (back to the top)
“Xerial employs advanced techniques to distribute resources across the platform through access points, all the while maintaining secure links to information profiles about a specific product or series of products. The distribution of data to multiple points across nodes is somewhat automated, based on server resource utilization.
The platform is continually measuring bandwidth and additional resources to alleviate server load by transferring resources to nodes across a global network of data centers. As demand shifts for a specific set of resources, network bottlenecks are minimized by dispersing the server load in high-usage areas throughout the nodes.
When resource use intensifies due to a surge in AP Traffic, patterns emerge that allow our services to store data across multiple data partitions. This is based on AI-driven predictive modeling constructed around user interaction.”
Database sharding on Xerial is a strategy in which a datastore, likely to exceed the resources available to a single storage node, is designed to scale based on access point data usage. This strategy is used to enhance performance by mitigating contention in the data store. For instance, if you were to design a service akin to Apple’s iTunes®, where you need to store and provide low-latency access to a vast array of audio and text-based information files, you might consider sharding by the genre of the artists.
Creating replicas of individual shards will facilitate on-demand availability. While the primary goal of sharding is to boost performance and scalability, it can inadvertently improve availability due to data partitioning.
Thus, the process of sharding involves multiplying the number of starting nodes for any set of data streams. This is done by increasing the starting points of operators based on direct filenames, each of which is held within its own protected memory space and/or physical data store. To test these points, we built our own tune player solution called Songtracks.
Songtracks was designed to handle song files or MP3/M4a files, MPEG video, H.264 Video in 4K, photographic data, graphics, and a communications layer, all within the same data stream that is dynamically assembled in the viewer app. A catastrophic event in one partition does not hinder an application from accessing data in other partitions. Moreover, an operator can perform maintenance or recovery of one or more partitions without making the entirety of the application’s data inaccessible.
Secure transaction utilize the ERC20 compliant smart contracts between parties to simplify the distribution of Tokens for services rendered in up to 9 decimals points, which enable a far larger number of service providers to provide scaled services as well as primary party positions in each payment ledger. When using smart contracts, the process for reporting transactions to the ledger to complete terms between parties is massively simplified.
The platform extensions do things like license validation between distributor and client nodes, as well as using dynamic shift on asset utilization throughout our network of MSC Nodes using IoT for things like load monitoring and QoS performance classes, while hyperledger creates the transparency between parties to conduct the business of things. This creates a unique, ground breaking, Hybrid Technology platform built around open standards and transparency between all parties involved. Reporting to standards associations such as MRC (Formerly SoundScan) keep all parties aware of actual listener and physical merchandise sales in a platform design with audit trails to every aspect of artists content. With each party to the smart contract capable of real-time reporting from never before accessible layers of revenue, traditionally utilized by the Label/Distributor.
Xerial is designed to record a Blockchain as an added security layer for securing the connection between each node used while assembling the user experience. The cost for storing transactions are relatively small (.20 apiece) and can be combined to cover transaction such as recording the purchase of a song, video, rental, or other protected data streams.
Secure transactions facilitated by Xerial technology utilize a #hyperledgerfabric to complete transactions between nodes, as well as between parties or organizations and nodes. Here’s a simple breakdown:
• Between nodes: Two exemplary nodes within an application might be a stream request and the database where the content to be streamed is stored. Though the transaction speeds (~15 per second) might seem slow, they create an immutable record that can be used to validate a data shard within the nodes.
• Parties and Organizations: This is defined as billing and licensing between the service provider and the recipient of the service provided.
• Parties and nodes: This is a feature built into the framework where the recipient interacts with a module to login to a service record. The app checks for any forks or branches in the ledger before authorizing a function.
Xerial is designed to request a Blockchain to be stored in a Linux Foundation’s Hyperledger blockchain with a secure connection between the licensing node of the application and the content viewer. This is done by receiving the original data from the transaction and using it to secure an unaltered license built off the transaction. The cost for storing transactions is relatively small (20 cents each) and can be combined to cover transactions such as recording the purchase of a song, video, rental, or other protected data streams.
When Xerial assembles each of a data store’s contents on the client app, the stored data is licensed by the end-user and becomes a “Party” in the hyperledger fabric recorded ledger transaction, before the unlocked view or licensed stream is opened. The recorded transaction becomes part of a collection of transactions stored in the ledger, demonstrating that the party’s transaction is validated. When a party transfers this license to another party, a fork/branch appears in the ledger, which our software detects as a transfer of license, thus disabling the original user’s access to that stream.
To prevent counterfeiting of streaming content, each stream has its own PISC to identify it within the ledger, and only the parties involved in the transaction can open a data stream from their device. We’ve designed an AI algorithm to identify which codes are already used in the system. When a new data store is requested, a new PISC is generated by the system with the option to store a license in the ledger.
Though blockchain records are not unalterable (given that forks are possible), blockchains are often deemed secure by design and represent a distributed computing system with high Byzantine fault tolerance. Transactions are trackable and can never be emulated or reverse engineered against the original data record stored within the Hyperledger Fabric.
Blockchains are typically managed by a peer-to-peer network for use as a publicly distributed ledger, where nodes collectively adhere to a protocol for communicating and validating new blocks. The code and the queried requests contained therein exist across the distributed, decentralized blockchain network. This approach offers better performance in the use of data shards for improved traffic flow, while also securing the dynamic assembly of the product or service experience at the user interface through a client app, rather than burdening the server with a rendered experience and attempting to push it to multiple clients simultaneously.

A Product Identifying Serial Code™ (PISC™) is fundamentally an alphanumeric string used to identify a product and its associated data, either physically or virtually, in analog or digital form.
The innovative application of QR Code® to develop PISCs is transforming the retail landscape. Many are unaware that a PISC can be constructed from any type of 1D or 2D barcode and, more crucially, forms the core of Augmented Reality information stores pivotal to the future of omni-channel marketing platforms.
A PISC is a data store identifier that uses a serial code, either numeric or alphanumeric, to pinpoint remote information stores. SerialCodes employ the PISC code™ much like a UPC-A, SKU, or other identifier to locate information stores related to a specific product at either the SKU level or individual level. The Serial platform exemplifies the simplicity of other Merchant Management Solutions (MMS), akin to the retailer point-of-sale system. However, the unique feature of the Serial Point of Sale is its ability to display an image, video or other graphical representation of the product associated with its PISC simultaneously with the product’s data. This enhances the customer experience by providing a richer understanding of the queried products.
Utilizing multiple independently managed data stores delivered directly to the consumer via a client-facing app/UI, the platform can handle heavier loads of simultaneous data streams through sharding. This approach paves the way for situating the point of sale system, organically linking the product or service directly from the product or service packaging, into previously unexplored territories. This revolution was made possible by overcoming the constraints of the hardware required to run the POS system from within the retailer’s brick-and-mortar location, allowing it to be operated from virtually any mobile device.
Continuous availability of on-demand data to the client-facing app, even after the QR Code® has been published, is ensured by dynamically assembled data stores. This fosters post-sale interaction opportunities between the brand manufacturer and the client.
Xerial can simultaneously manage a wide range of information at the individual product level. An excellent illustration of this is the concurrent management of data sets using a vehicle identifier like the vehicle VIN (information specific to that vehicle) and data stores that provide a generalized view of the vehicle model’s features. While both sets of information are consumer-relevant, each holds distinct values influencing consumer decision-making.
Consider Xerial in this way: a single PISC is used for managing individual data stores related to a specific vehicle (for instance, remaining oil life or station shortcuts on the vehicle’s sound system), while another data set includes model-specific information such as type of oil (10W40), available radio services (like On-Star® or SiriusXM® Satellite Radio), or other information pertinent to the overall specifications.
The platform manages both sets of data across several industries represented on the main Xerial Assembler™ page.
Xerial Codes transmit information stored in the respective data record, relevant to the vehicle, while managing and disseminating that information to multiple users simultaneously. This process resembles the “Wheel and Spoke” network architecture around which a social media platform is built, while maintaining platform/device agnosticism.
Recognizing that traditional SKU-based register points of sale were being used by merchants to locate products within the retail supply chain, we designed a b-Channel solution to provide access to information stores targeted at the consumer in a Merchant Managed Platform (MMS). This approach was aimed at crafting and managing the consumer experience.
A QR (Quick Response) code is a type of matrix barcode (or two-dimensional code) designed to be read by smartphones. It encodes information in both vertical and horizontal directions, unlike the traditional barcodes which are one-dimensional.
Each QR code consists of a grid of tiny squares that can either be black (representing 1) or white (representing 0). These grids are parsed in groups to represent certain values, usually in a binary form, like “1, 2, 4, 8, 16, 32, 64, 128”. The combination of these squares can represent characters, such as letters or numbers, according to established standards like ASCII.
When a QR code is scanned, the reader converts these patterns into data. For instance, groups of squares can correspond to specific characters. A sequence of such characters might form a URL, which directs the scanning device to a specific website or piece of information.
QR codes have a high storage capacity. Depending on the version and error correction level, they can accommodate over 4,000 alphanumeric characters. This makes them versatile for a variety of applications, from simple product identification to storing web addresses or other data.
| Character | Hex Value |
|---|---|
| f | 66 |
| g | 67 |
| h | 68 |
| i | 69 |
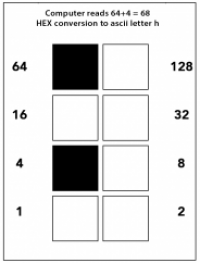

A QR (Quick Response) code is a two-dimensional matrix barcode that can store data, often represented as specific patterns of black and white squares. When decoded, these patterns translate to alphanumeric characters or other data sets.
To illustrate, the number 68, when stored in a QR code pattern, can be represented by marking the boxes equivalent to the sum values (4, 64). When decoded, this can correspond to the hexadecimal value of the letter ‘h’, such as in the beginning of a web URL like ‘http://’.
Consider the XerialCode Identifier as an example. Its QR Code contains the Product Identifier value ‘xerial=maWUkZWkIZQ=.xtem’, ending with our unique security algorithm extension. Each XerialCode has a unique identifier, generated by the enterprise extension manager during an edition run. Enhancing its security, the Product Identifier Serial Code (PISC) is registered with the Library of Congress under copyright laws, deterring unauthorized duplications.
QR codes have vast storage potential. For perspective:
Numeric only: Up to 7,089 characters.
Alphanumeric: Up to 4,296 characters.
Byte/binary: Up to 2,953 bytes.
Kanji: Up to 1,817 characters.
These capacities pertain to the largest standard QR codes with minimal error correction.
However, the main advantage of QR codes is their versatility. A QR code encoding a URL can link to extensive online data, potentially encompassing gigabytes or dynamic content. As technology progresses, QR codes may offer even greater capacities and functionalities.
A product identifier, serving as a unique code for products, could be etched onto the product, printed on its packaging, or included in related marketing materials. It’s relevant to both tangible and digital products.
Think of the Xerial platform as transforming your smartphone into a sophisticated cash register. But instead of scanning barcodes to retrieve typical Point of Sale (POS) details like price or inventory, you’re diving deeper.
By simply scanning the product identifier with your device’s camera, you access a rich cloud-based resource of information right on your smartphone.
Xerial empowers brands with tools to craft and manage the data linked to their products. As consumers interact with a product, it’s this unique connection between the product and its serial code—what we term the PISC—that facilitates access to detailed product information.
Our platform maintains a seamless connection between these unique codes and the extensive data-stores of product details. This ensures that when a consumer uses the Xerial mobile app, they enjoy an enriched, product-specific user experience.
More than just a standalone system, Xerial is an integrated extension of traditional Enterprise Resource Planning (ERP) systems. It ushers in new opportunities across pre-sale, at the point of sale, and post-sale phases. Brands can amplify their marketing and commerce strategies without the need for a complete infrastructural overhaul.
In essence, think of barcodes as bridges. They link to unique identifiers that in turn connect to data warehouses. The particular warehouse you reach is contingent on which entity’s database you’re linked to.

There can be as many data stores that a single barcode is capable of pointing to as there are web addresses on the internet. Xerial is now merging WebOS and MetaOS into a hybrid framework of information management tools that point to a fully managed cloud-based enterprise data management platform for alternative information views on products and services with customizable Augmented Reality Data Tools. (ARDT)
Brand managers are beginning to realize that UPC-A codes (USA version of UPC Codes) are the barcodes that you see in on the back of virtually all packaging sold through POS systems (Think can of Campbell’s® Chicken Soup) have the specific purpose of identifying the product within the MMS, while delivering critical details about the products stock, price, warehouse location etc.
This provides an organic or natural link to the product represented by the barcode used to identify its location in the supply chain. Typical MMS systems only focus on the core aspects of the product lifecycle which include financial, supply, operations, commerce, logistics, manufacturing, and human resource activities.
The Xerial identity mechanism is essentially what has built the global commerce system where barcodes on different types of products like the EAN code for Magazines and other Copyrighted published works, as well as 27 other types of barcodes are used in everything from Banking in Switzerland to ticketing for concerts and train rides.
Barcoding has been used throughout many industries as identifiers to data related to commerce and transactions of those goods and services. All Barcodes can essentially provide the same linking to product information as the QR Code, based upon their built-in purpose to identify a given product through a registered common identifier.

- Develop and Patent technology used for viewing universally acceptable, common identifiers to link products to information data stores. This is what is called the PISC or Product Identifying Serial Code.
- Create software tools that enable brand or service providers secure links to data stores capable of delivering rich media like product photos and streaming video/audio content. The user experience must be built in such a way that the experience and QoS (Quality of service) rivals that of other industry leaders. This is called the service backbone where data handlers, and content management techniques are used to deliver your information to the viewer. This makes up the bulk of Xerial’s enterprise suite.
- This service must be built from a framework that supports extensibility to stay modern and allow for customized modules that fit your client’s needs.
- A client viewing app that assembles each of these data stores in a beautiful UI that houses all the features that most modern social media apps feature, with cutting edge features that get your customer to want to interact with brand targeted marketing.
Because only a limited amount of data can be shown in a UPC or Code 128 barcode, the application can predetermine the URL of the datastore and just provide the datastore ID from the numerical representation of the 8, 12, or 13 digitally stored on the barcode and when the URL is predefined, the PISC provides the addressing mechanism to locate the data-store ID, which is used to render its product data to the requester.
This discovery led us to file for Patent Protection (The 9892440 Patent) for the methods used in our software to compare product identifying serial codes. This was made by research development team, filed in 2014 and Patents were granted in 2018. You can review how PISC’s are used in several of our application designs by going to XerialCode Products links in the menu or visiting the modules below to see the customizable APIs we have or are in the process of developing.
The PISC code technology design and Patent.
Michael Wright, the company founder developed the technology used in PISCs or “Product Identifying Serial Codes” and was granted a US Patent #9892440 for methods used in the software development, that make the functionality possible.
The technology is built around a gatekeeper concept where there are two types of user ID’s to fulfill the actions of comparing the product code. The technology encompasses both the first user (administrator) who first logs-in to the server to upload data, and a second user (customer) who uses his/her smart device to scan and view remote stores of data related to that specific products data. When the code is matched, it acts like a gate that unlocks to enable the next set of instructions to move forward.
A second user ID does have to come from a physical person where data automation requires the second login. The second user could be as simple as an automated script that sends login information over a cellular radio device to the cellular radio tower to identify the radio device on the network. Techniques like this have been used by law enforcement to track a cell phone through triangulating the last known position of that device via cell towers to identify the devices last known location on the network. Feel free to visit the FCC on this subject at the following site: https://www.fcc.gov/oet/ea/granteecode
Any time you turn on the device, it is sending its location to the cell tower, and is just another way to identify which user and which credentials are used to gain access to the product being queried. If the second user does not possess the User A credentials, the system treats the user as a client without administrator rights to that products data store in view mode.
Patents are process oriented, not time oriented, that is for at least 27 years.
If a user views data on a TV, they must log into the service and register payment for that service like on-demand movies, monthly subscriptions and content usage, a PC? Log-in when you create your use account to open the PC with or without a passcode, PDA or Tablet, same thing. Logging into a system can also incorporate user credentials that you input by typing on a virtual keyboard on the imaging device or in this case, the LCD/LED screen. This provides the visual feedback most people need to visualize their input.
The proof of concept and traction are that there are hundreds of brand companies already using the technology to provide access to a wealth of product information using the PISC as its product identifier. When an object is identified and a data store related to that product is used to deliver information related to that product, it is using the PISC regardless of how that data is being displayed. Through a browser, an app or as part of a third-party API.
Xerial is built on top of a series of Cloud frameworks that utilizes A RESTful API — also referred to as a RESTful web service or REST API — based on representational state transfer (REST), which is an architectural style and approach to communications often used in web services development. This means the APIs can also be built using dynamic languages such as JavaScript (ECMA Script) as well as Python and PHP.
The REST used by browsers can be thought of as the language of the internet. With cloud use on the rise, APIs are being used by cloud consumers to expose and organize access to web services. REST is a logical choice for building APIs that allow users to connect to, manage and interact with cloud services flexibly in a distributed environment. RESTful APIs are used by such sites as Amazon, Google, LinkedIn and Twitter.
A RESTful API uses commands to obtain resources. The state of a resource at any given timestamp is called a resource representation. A RESTful API uses existing HTTP methodologies defined by the RFC 2616 protocol, such as:
GET to retrieve a resource;
PUT to change the state of or update a resource, which can be an object, file or block;
POST to create that resource; and DELETE to remove it.
Data formats the REST API supports include:
application/json (Easier to understand, but limited to addressing modules using standard text and numbers)
application/xml (Supports more than letters and numbers but more difficult syntax)
application/x-wbe+xml
application/x-www-form-urlencoded
multipart/form-data
Xerial passes these methods back to the core framework (Larevel, Yii2, Django for Python related integrations, Pods for Swift, Ruby for extensions to IOS and Android and scores of other objects for use in object oriented programming) transferring information requests back to the host, which responds to the requestor for reassembly on client facing application.
Xerial uses multiple frameworks and creates translators between many of them to manage much of the utility work while enabling its customization modules to be purposed into creating the data-store for each client wanting to use the system generated PISC to link back to the framework.
At the heart of the Xerial architecture is the customization modules, written in Javascript and PHP created to easily save and retrieve data from the SQL Based data store. The primary connection point between the client/server is http which is used in methods similar to creating and managing rich media posts similar to a Tweet for text, or Facebook for Audio, Video, and imaging data streams and handlers. There is much more about how the system creates and manages each transaction between the server and requestor, but that will be posted in the future.
The platform assembles server resources around content that is comprised of modules and extensions that are compiled together into a series of ‘services’ each respectively created for a specific task targeting many areas of commerce with each respective field the content is generated for. As a service, Xerial(ERPe) manages the data load to each using sharding techniques to offset peak loads to server resources. (More to come)
What is the difference between a (M) Module and a (T) Template? – Modules are single functional utilities that can be used standalone or in combination when used as a component for a template project. A Template is simply a formatted combination of modules that are tied together to develop rich or full applications that require different functions that each module provides. When combined into a template, the functionality is usually designed to provide a series of services for specific segments of a marketplace. See example below:

Audio Manager (M) – Input for managing audio content for non-commerce related transactions. Use the audio manager to embed audio file playback functions on any portion of your Pisc. This core API includes advanced playback tools, and GUI or Graphical User Interface elements and function for your app.
iTunes® and Safari are trademarks of Apple Computer, Inc. Registered In the USA and other countries.
Opera® is a trademark of Opera Norway AS. Registered in the USA and other countries.
IBM® is a trademark of IBM Inc. Registered in the USA and other countries.
Chrome® is a trademark of Alphabet, Inc. Registered in the USA and other countries.
Explorer® is a trademark of Microsoft Corporation. Registered in the USA and other countries.
Facebook ® is a trademark of Meta. Registered in the USA and other countries
Linked-in® is a trademark of LinkedIn, Inc. Registered in the USA and other countries.
Compuserve® is a trademark of Compuserve, Inc. Registered in the USA.
Campbell’s Soup is a Trademark of Campbell’s Soup Company, registered in the USA and other countries.
On-Star® is a trademark of OnStar LLC, Registered in the USA and other countries.
SiriusXM® is a trademark of SiriusXM Radio, Inc, Registered in the USA and other countries.
QR Code® is a trademark of Denso Wave, Inc. Registered in the USA and other countries.
Twitter® is a trademark of Twitter, Inc. Registered in the USA and other countries.
AOL® is a trademark of Oath, Inc. Registered in the USA and other countries.

Incredible take!